![]()
I make it a habit to learn as much as I can from others, so every week I listen to an assortment of podcasts covering topics such as leadership, communication, techology, security and more.
![]()
I make it a habit to learn as much as I can from others, so every week I listen to an assortment of podcasts covering topics such as leadership, communication, techology, security and more.
![]()
I make it a habit to learn as much as I can from others, so every week I listen to an assortment of podcasts covering topics such as leadership, communication, techology, security and more.
![]()
Welcome to my new site! After spending quite a bit of time away I decided it was time to get back to writing, researching, and contributing again. For a number of reasons, I did not want to continue with my traditional hosted Wordpress site. I wanted something simple, fast, and cost effective so ultimately I landed on a static website generated in Hugo and hosted on Amazon S3.

I had been wanting to take the Cracking The Perimeter (CTP) course for some time but my schedule was pretty hectic. I finally forced myself to start it at the beginning of the new year and I’m really glad I did. As promised, here is my review…
![]()
I just wrapped up the Offensive Security Cracking The Perimeter (CTP) course and one of the topics was AV evasion. Although I write a lot of custom scripts and tools, when it comes to AV evasion, I typically rely on the tools and methods of others (Veil, powershell, python, custom shellcode). That said, the great thing about courses like CTP is they give me an excuse to investigate a topic that I haven’t had an opportunity to delve into in much detail.

A while back I introduced the EggSandwich in my tutorial on Egghunting as a means to implement some basic integrity checks into the traditional Egghunter and overcome the problem of fragmented / corrupted shellcode. I recently took the opportunity to update my implementation so it could accomodate shellcode of any size. The code and a brief explanation follows.
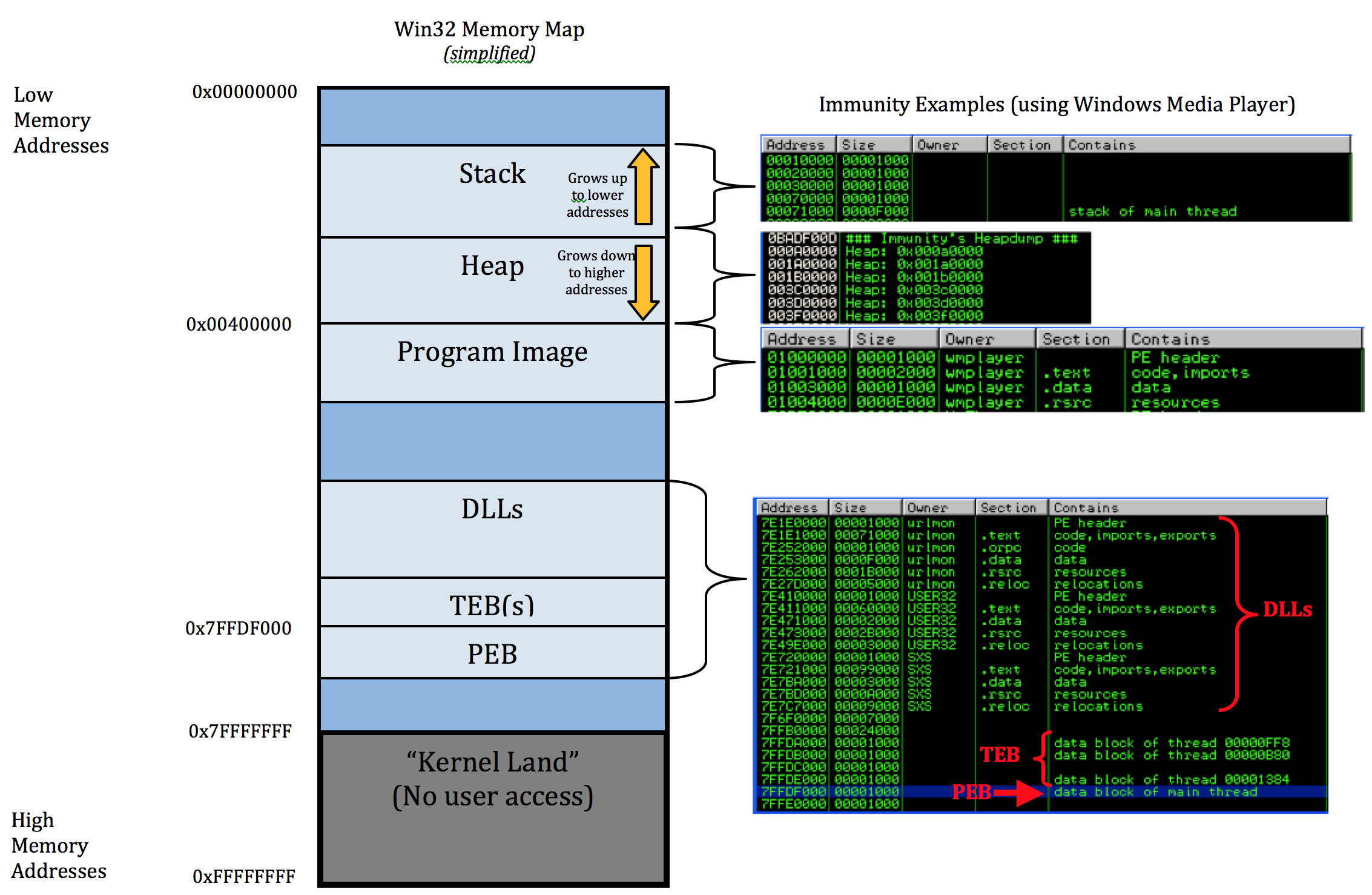
Welcome to Part 1 of a series of posts on Windows Exploit Development. In this first installment I’ll cover just the basics necessary to understand the content of future posts, including some Assembly syntax, Windows memory layout, and using a debugger. This will not be a comprehensive discussion on any of these topics so if you have no exposure to Assembly or if anything is unclear after you read through this first post I encourage you to take a look at the various links to resources I’ve…

Recently I took the Offensive Security Penetration Testing with Backtrack (PWB) course, passed the exam, and achieved the OSCP certification. I learned a ton and earned my most rewarding cert yet. There are several great reviews of the course but I figured I’d provide my perspective.