Introduction
In Part 1 of this series, I talked about what I see as two equally important components of a security program – To Protect and To Enable. The Protect component is what many people probably think of when they consider the role of a security program. But CISOs and business executives alike should also consider how an enterprise security program can enable an organization in meeting its strategic objectives. For that, a CISO should align the security program with the needs of the business and find ways to deliver value that extend beyond the traditional preventive security controls. Yes, the business absolutely needs those too, and they’re still a fundamental part of the security program, but there’s also an opportunity to deliver value in other ways.
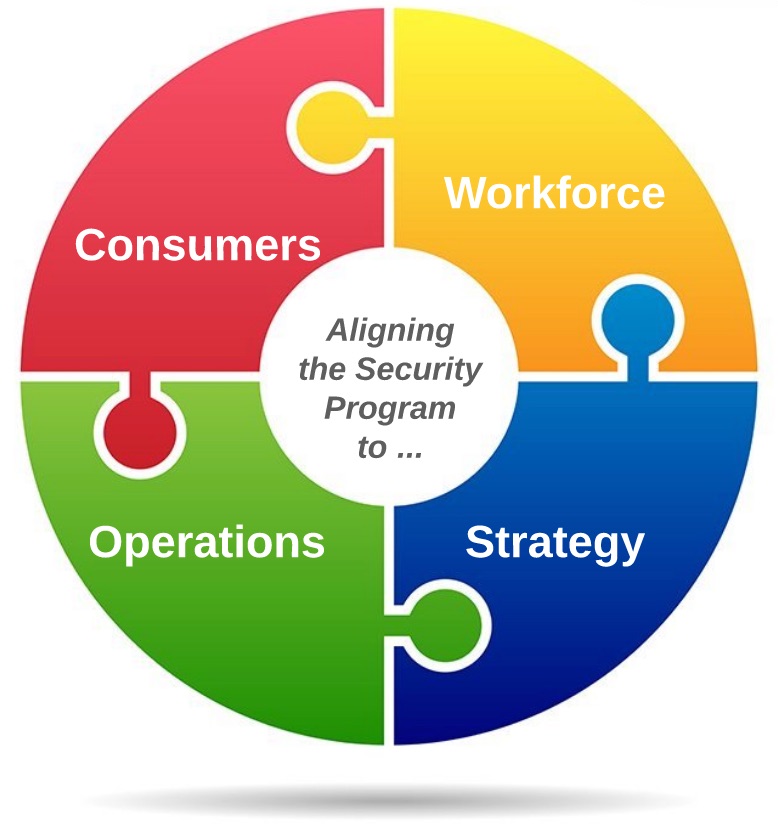
I’ll present some ideas of how a program can become more business-centric by looking at it through the lens of the Consumer, the Workforce, the organization’s Strategy, and critical business Operations.
I’ll also discuss why it’s not just the CISO that plays a role in ensuring the security program is delivering value to the business.
Providing value to Consumers
Most organizations (profit and non-profit alike) provide some products and/or services to an external consumer, and CISOs should be thinking about how they can contribute to a better consumer experience. Of course, protecting consumer data and safety should be a fundamental focus of any security strategy, but there are other opportunities as well.
Let’s assume for the sake of example, your organization develops a consumer facing, web application. You could think of ways that security can play a role in 1) enabling faster delivery of that product 2) enabling a higher quality product or 3) providing fundamental or differentiating product features.
Faster Delivery of Higher Quality Products
Security should be treated the same as any other factor of quality in the software development process. Products with built-in security are more reliable than those that are riddled with insecure code. Embracing a shift-left approach and embedding automated security testing into the DevSecOps pipeline will not only make it an inseparable component of product development, but it can also eliminate manual reviews, accelerating time to product delivery – meaning you can get a better quality product into the hands of the consumer faster.
Delivering improved product features and consumer experience
You may also want to think about how security-related features and design can improve the consumer experience or deliver key features that your customers are expecting. Think about something like Customer Identity and Access Management (CIAM). Authentication is often one of the earliest interactions a customer will have with your product, and bad experience can leave the wrong lasting impression. Is your underlying infrastructure able to support peak loads to deliver the best performance? Are you thinking about how your SSO strategy can provide a more seamless experience across all of your products and services? Are your customers expecting MFA or support for social login?
A comprehensive CIAM strategy goes beyond just authentication and could include performance optimization features like cached content and API prioritization. It could also include features like profiles, preferences, and behavior analytics to deliver customized experiences and provide better insights into consumer interactions with your products and services.
The opportunities to provide value to the consumer can vary by organization or product. CISOs and their security teams should engage with product and service teams and other business stakeholders to seek out those opportunities.
Providing value to the Workforce
The workforce is also an important customer of the security program and CISOs should aim to deliver the best possible experience, whether it’s through eliminating existing “pain points” or introducing new capabilities.
In my opinion, the best way to figure out what the workforce needs is to just go and talk with people (at all levels). When you’re having these conversations, don’t lead with security topics or jargon. Talk to them about their priorities and day-to-day operations. Get an understanding of their workflows and how they interact with technology and data. Ask them about what frustrates them. Ask questions like “If there was one thing you could change, what would it be”? Unfortunately people sometimes just accept an imperfect process or workflow as something they “just have to live with” and won’t surface the issues until someone asks them.
I prefer face-to-face conversations whenever possible. You might also consider using surveys to gather data from large numbers of people and establishing on-demand feedback mechanisms so that ideas and issues can be raised by anyone, anytime – just don’t use these in lieu of one-on-one dialogues which can lead to more valuable feedback.
You never know what you’ll learn or implement as a result of this feedback. From my experience, resulting projects could include a wide range of activities including process re-engineering and automation to remove bottlenecks, improved authentication to improve experience, cloud-based file sharing tools to facilitate external collaboration needs, policy changes to eliminate unnecessary restrictions, updated technical controls to reduce negative business impact. In fact, I’ve implemented new, unplanned initiatives that improved workflows for thousands of employees just from having these conversations with a few people.
Ensuring Operational Resilience
Operational disruptions are costly to the organization and can have wide-reaching impact to customers, business partners, or investors. A best practice security program should have a strong focus on ensuring operational resilience.
While a big part of a CISO’s role in operational resilience involves ensuring adequate protect, detect, and respond capabilities, it could also involve redesigning business processes, developing business continuity plans, rearchitecting for fault-tolerant, highly available systems, or ensuring sufficient data/system backup and recovery. Business stakeholders may not fully appreciate the potential impact of cyber risks or they may make incorrect assumptions about what would or would not be impacted in the event of a major incident. Perhaps one department’s systems are resilient to disruption but they rely on an upstream data source that isn’t. Sometimes even business units within the same organization aren’t communicating about these issues, so the CISO can help bridge that gap and identify opportunities for improved operational resilience.
Not all systems and data are of equal importance so CISOs need to engage with business stakeholders to understand the most important workflows, systems, and data, and prioritize the operational resilience efforts accordingly.
Enabling the Organization’s Strategy
Strategic initiatives may introduce fundamental changes in the way people work, new operational support requirements, or new risks. Is your organization thinking of developing a new business venture, entering a new market or acquiring another organization? What could the security barriers or regulatory implications be and how can those be adequately addressed? Does your current user access strategy support it? Will it require new system integrations or data sharing? Are there actions you should take early in the process to prevent implementation delays?
Many organizations are also embarking on a digital transformation strategy which warrants involvement from the security program on many levels. Take for example, the adoption of hybrid cloud where there are so many key security considerations that if the CISO isn’t involved from the start, you may risk major problems or delays. However, if planned and implemented properly, building in security from the start (while taking into account business use cases) can result in a more reliable cloud environment that closely aligns with the business needs.
Designing new business workflows, hybrid cloud architectures, system integrations and security controls can’t happen overnight. Security is most successful when it’s proactive, not reactive – being a part of these strategic discussions and planning efforts early can eliminate unnecessary delays as well as help identify and mitigate unforeseen risk before it’s realized.
Sometimes business alignment requires changing the way you work
The value that a CISO’s security program delivers (or is perceived to deliver) can be impacted by how responsive that program is. If everyone else is operating on a sprint-based schedule and delivering value every 2-4 weeks, it can’t take the security program 12 months to do the same. If other parts of the organization have adopted agile, consider adopting agile too. Even if you have to adapt your implementation, perhaps there are opportunities to implement Scrum and sprint planning for some areas of the security program and Kanban for others, with a goal of continually delivering incremental value whenever possible. Even if initially the net result is the same, delivering some noticeable value more frequently can help change the perception of the security program.
Also, the CISO should look across the security program for process improvement or automation opportunities that can help reduce delays or eliminate non-value-added work. Timely communications and good customer service are fundamental to being perceived as a business enabler so it’s important to assess those areas and make adjustments, if necessary. In other words, don’t just think about what the security program is doing, also consider how it operates. Just remember that automating bad processes just leads to faster bad processes, so really take the time to examine how you work.
Is being “business-centric” really a sign of CISO maturity?
I’ve heard terms like “Business-Minded” or “Business-Centric” CISO and I’ve seen them used as indicators of CISO “maturity” (on a scale where “less mature” CISOs are identified as “governance-centric” or “technology-centric”) – but I don’t think looking at it as a sign of CISO maturity is entirely accurate. Frankly, every CISO should be business minded (not just “mature” ones), but how much time a CISO is able to spend on enabling the business can be heavily dependent on the maturity of the organization too. While the CISO absolutely must proactively seek out ways to align the program with the business, I see it as just as much of a sign of program and organizational maturity.
As a CISO, you need to focus on the things that your organization needs most at the moment. Perhaps you’re stepping into an organization with a brand new security function that has very little in the form of established policy and standards so you have to spend more time on governance. Perhaps you have little in the form of preventive technical controls and need to focus your attention there. These things don’t mean you’re not a mature CISO, it means the security program isn’t mature and you’re focusing your attention on what is needed the most right now. Assuming a CISO has limited resources, a situation where there are zero ransomware protections probably deserves more attention than seeking out ways to improve the experience for an employee-facing workflow.
That said, even if a less mature security program requires that a CISO focus more attention on establishing fundamental security controls, I still recommend not completely losing sight of the business and spending whatever time possible to engage in conversations with business stakeholders and identify opportunities to Enable the organization.
It’s not just the CISO – the organization plays a key role too
While the CISO must actively engage and align the security program with the business, if the organization does not view the security program as a key business function at the same level as Finance, Legal, or IT, it’s unlikely that even the most business-oriented CISO will be as successful as they could be.
Finding ways to deliver better products or services requires security teams to be an active part of conversations that aren’t centered around just traditional security discussions. Ideation, journey mapping, requirements discussions are all opportunities for security to consider how they might add value. Ideally the security teams are invited to those discussions as a matter of practice and not just engaged when it’s time to talk about “security stuff”.
The security program has an impact on nearly every part of the organization and the CISO really should to be part of strategic, operational, and product discussions. Key shifts in strategy or initiatives such as exploring emerging markets, acquisitions, or new service offerings, can’t “trickle down” and CISOs should be finding out at the same time as other key executive stakeholders (CFO, CIO, etc.) to determine what, if any, risk, key enablers, or changes to the security strategy are necessary or possible. The business should consider if something is going to impact people, processes, technology or data. If so, there’s at least a chance the CISO may need to play a role.
There was an article that appeared in the fall 2020 issue of the MIT Sloan Management Review titled “Make Cybersecurity a Strategic Asset” that was very relevant to this topic. I won’t rehash the entire article here (and suggest it as an additional read), but it identifed four reasons why “executives fail to recognize cybersecurity as a strategic priority, even as many have embarked on digital transformation strategies”:
- Cybersecurity is delegated to IT
- Companies misunderstand the strategic nature of cybersecurity risk
- Companies keep attacks under wraps
- Executives assign strategic priorities based on their own areas of expertise
The first is one of the reasons I dislike the term “IT Security” – which tends to view the security program through the narrow lens of technology and can unintentionally limit the ways in which it’s seen by the rest of the organization. While that is how many security programs got their start (and so much of the narratives are still often centered around the latest technical vulnerability), modern security programs should also be customer-centric and focused on ensuring operational resilience.
When it comes to the second reason, the article points out that in addition to mitigating threats to earnings and operations (i.e. resilience), “a mature cybersecurity strategy … can reveal new strengths and fundamental weaknesses in leadership teams and organizational capabilities”. In addition, some of the companies researched “found that it paved the way to a fully digital business model or helped them create a new value proposition around security for customers”.
The third reason is an unfortunate reality. Cyber attacks that are not shared are missed opportunities to learn from others and to illustrate how big of a risk it is to organizations of all industries. You often hear “never waste an incident” because, although CISOs hate to see other organizations affected by a major threat, publicized incidents are often opportunities to get support for additional resources or initiatives. The reality though is these incidents are happening all of the time, whether they’re publicized or not and organizations should not be waiting for a news story to view security as a key strategic enabler.
As for the fourth reason, I think it’s expected that people’s views are shaped by their knowledge and experiences. It’s the same reason that user security awareness is so important, yet can be so difficult. If someone doesn’t appreciate the threat, understand the topic, think something can happen to them, or relate to it in any appreciable way, it’s difficult to get them to change their behavior or see value it something. Relating security to business strategy can pose the same challenges. There may be regulatory implications, data residency requirements, new threats or vulnerabilities, business continuity requirements, or a host of other things that could require additional risk mitigation from the security program. Or maybe there are unbudgeted user- or technology-driven security costs that need to be accounted for. Or perhaps the security program can deliver unforeseen value to a new product or service. But without involving someone with that knowledge and experience, these things could go unnoticed. That’s why it’s important to have the CISO participate in strategic and business-centric conversations early and often in order to represent their area of risk.
Ultimately, I think there is benefit in taking a look at whether any of these are relevant to your organization and think about how to reframe the security program as a business enabler that can deliver value, support strategy and ensure operational resilience.
What’s Next?
Hopefully in this installment I’ve provided a few ideas on how a CISO can position the security program as a business enabler and illustrated why it’s equally important for organizations to view the security function as a strategic priority.
If you haven’t caught the rest of the series, you can find them here:
-
Part 1 - I gave a brief background on how I became a CISO and outlined the process of defining the security program’s purpose and mission statement.
-
Part 2 - I talk about scoping and organizing the program.
-
Part 3 - I kick off the discussion of program metrics, by introducing the concept of measuring Capability and why it’s important.
-
Part 4 - I continue the discussion on metrics, focusing on how to measure program Performance and how to present your metrics to executives and other stakeholders.
In upcoming posts I plan to cover topics such as measuring risk, budget planning, and more. Stay tuned for those, but in the interim I enjoy connecting with and learning from others, so reach out to me on LinkedIn and Twitter.