Whether its’s for a bug bounty or a penetration test, it’s very important to demonstrate the impact of a vulnerability. Not only do most organizations have limited resources and competing priorities (so turning over a report with a long list of low impact vulnerabilities isn’t very helpful), but in the case of bug bounties, it also dictates payouts.
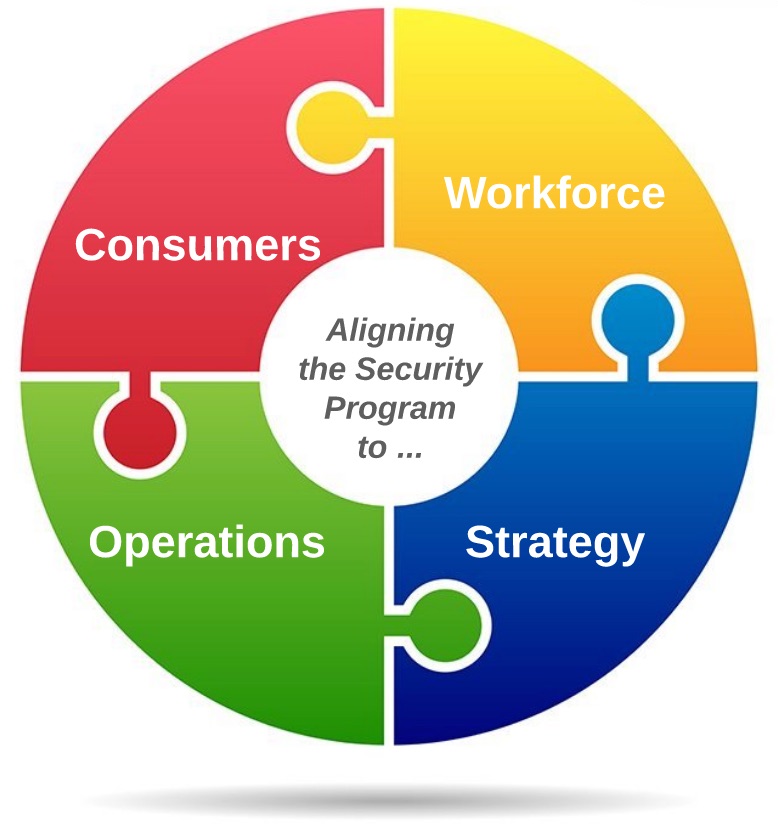
In Part 1 of this series, I talked about what I see as two equally important components of a security program – To Protect and To Enable. The Protect component is what many people probably think of when they consider the role of a security program. But CISOs and business executives alike should also consider how an enterprise security program can enable an organization in meeting its strategic objectives. For that, a CISO should align the security program with the needs of the business and…
![]()
Welcome back to the fourth installment of this series on designing, managing and growing a successful security program. Today we’re continuing the discussion on metrics, this time focusing on how to measure program Performance.
![]()
One of the highlights of my career has been the opportunity to serve as a CISO, designing, managing and growing a successful security program. Through this series of posts, I’m sharing some of the things I’ve learned along the way.
![]()
One of the highlights of my career has been the opportunity to serve as a CISO, designing, managing and growing a successful security program. Through this series of posts, I’m sharing some of the things I’ve learned along the way.
![]()
I make it a habit to learn as much as I can from others, so every week I listen to an assortment of podcasts covering topics such as leadership, communication, techology, security and more.
![]()
I make it a habit to learn as much as I can from others, so every week I listen to an assortment of podcasts covering topics such as leadership, communication, techology, security and more.
![]()
I’ve had the amazing opportunity and privilege as a CISO to lead a team charged with designing, managing, and growing a successful security program. I realize that many don’t get the opportunity to design a security program from scratch and I’ve learned a lot along the way so I wanted to create this series of posts to share that knowledge. I don’t have all of the answers and the approach I took is certainly not the only viable one – but whether you’re tasked…
![]()
I make it a habit to learn as much as I can from others, so every week I listen to an assortment of podcasts covering topics such as leadership, communication, techology, security and more.
![]()
Over my career and certainly during my time as a CISO, I’ve come to value the importance of authentic, purpose-driven leadership. These days I spend just as much time thinking about how I can improve my leadership skills to better serve those around me as I do on the functional and technical aspects of my job.


